HI everyone,
Recently a DDOS attack was launched on DNS Server of Dyn[ref]https://www.theguardian.com/technology/2016/oct/26/ddos-attack-dyn-mirai-botnet[/ref]. It brought many websites down[ref]http://www.cnbc.com/2016/10/21/major-websites-across-east-coast-knocked-out-in-apparent-ddos-attack.html[/ref]
In the meantime, a friend of mine was also attacked and his account was also used to launch a DDOS attack. He was hacked on 19th October and the large scale attack on DYN servers were launched on 21st October. I’m pretty sure that he also would have become the part of same botnet which launched the attack on Dyn servers had DigitalOcean not blocked him. His network usage was at peak of around 250Mbps for around 2 hours after which Digital Ocean shut down his virtual machine and notified him regarding the problem.
The attack was nothing major but it was simple plain on old dictionary attack and they finally managed to get root access to his system for 2 reasons:
- He had setup a weak password: hisname123
- He had only one user account on his system which was “root” and he had enabled password based login for that.
- He was using default ssh port.
My friend told me about the hack a few hours after digital ocean notified him and I decided to look at the logs. But I thought that if the hackers had gained root access on his system then they should have removed the logs as well but it was not the case, logs were there intact and from that we could traceback the whole attack history. I have uploaded the authentication log files[ref]Authentication Logs download link[/ref] and you might want to have a look at them.
This is the screenshot of the email which my friend received from digital ocean.
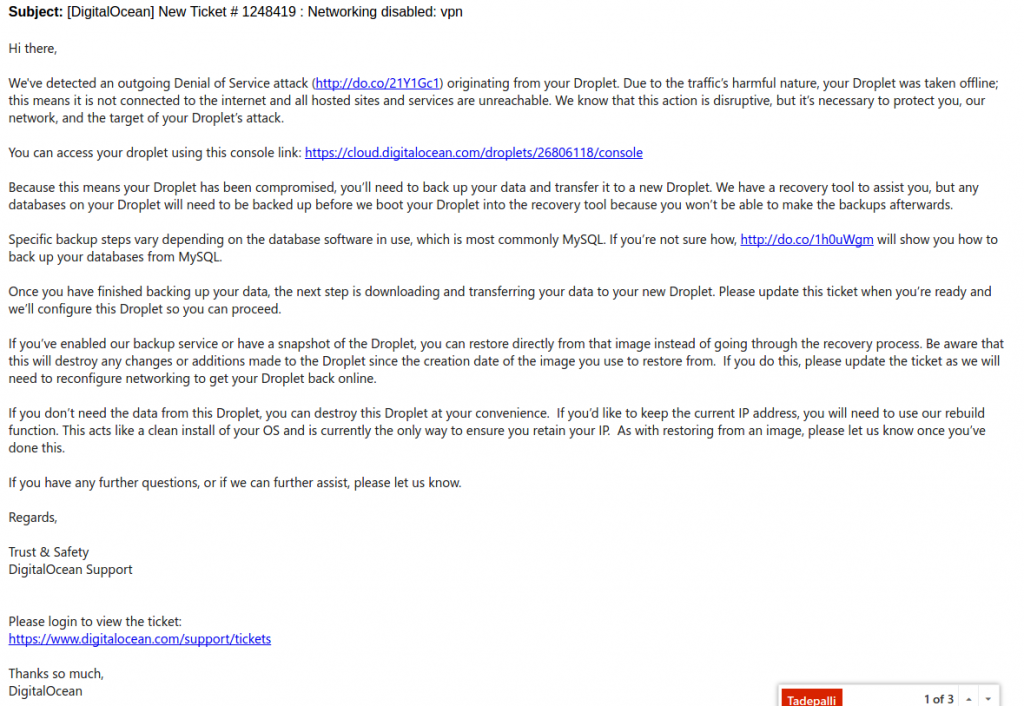
Thankfully digitalocean was very cooperative in resolving the whole matter. Even though they had blocked his VM, they gave him a recovery machine and mounted his files on that so that he could recover all his important files and because of that we were able to get the log files which surprisingly were intact.
After looking at the logs I found that they were trying to launch this attack for more than a month. They used to try random username and password from different IP addresses. I’m sure that they don’t own those IP addresses and they are running those attacks from compromised machines.
These script kiddies have automated scripts running which keeps launching the dictionary attack. And for them the machines on digitalocean, AWS or other cloud providers are high value targets because they can get speeds upto 200-300Mbps from a single machine.
Ok I get it, but how can I prevent myself?
A simple workaround to prevent yourself is to set a powerful username and password but if you are too lazy to do that then just change the default port for ssh (Though I won’t recommend keeping a weak password). The ideal solution would be to setup a powerful password + change the default port for ssh. Please remember that your SSH port can be discovered using port scanning so don’t rely on that completely.
UPDATE 1:
You can also install fail2ban on your server. It blocks the malicious IP addresses which try to launch brute force attack by monitoring your log files.
UPDATE 2:
I completely missed ssh key based authentication. You can use ssh keys to login to your VM and not allow password based logins (As suggested by one of the readers). That will prevent you from brute force attacks. You can refer to this link to set it up.
UPDATE 3:
As one of the readers suggested: Here are some good practices to secure your openssh server.
http://www.cyberciti.biz/tips/linux-unix-bsd-openssh-server-best-practices.html
And for my college friends and juniors who are just getting started with using these cloud services, there are a whole lot of things that you need to do to ensure security on your machine. So if you are planning to install a OpenVPN Server then you also need to know how to secure your VM from attacks because if your machine is compromised and used to launch some attack then you are the one who will be liable for it (to some extent). 🙂