Hi everyone,
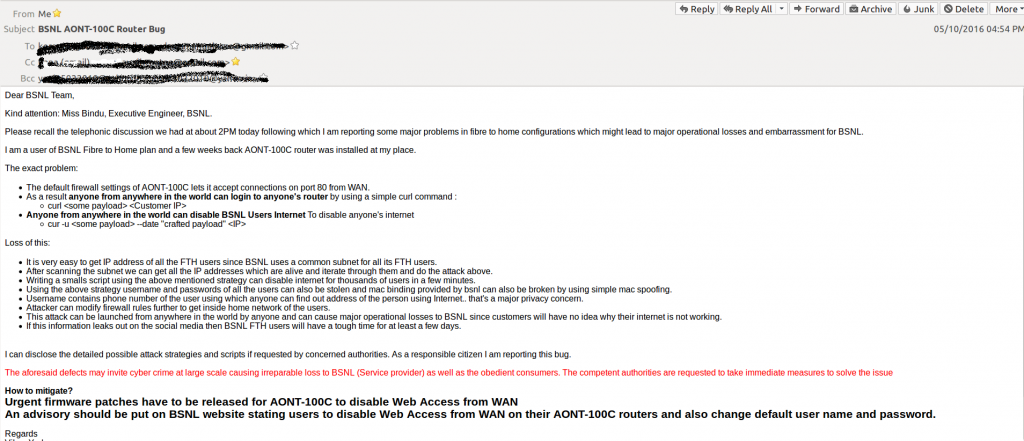
It’s been more than 5 months since I reported BSNL about a major problem with their FTH modems. It’s a very small issue but poses a serious threat to user security. Since BSNL decided not to heed to my requests, I have decided to disclose the problem out in the open so that the users can prevent themselves. I am also attaching the screenshots of my the emails which I have sent to various people at BSNL.
Problem Description:
BSNL uses AONT 100C (It is manufactured by a company named Alphion) modem to provision fiber to home service. They forgot (or maybe intentionally disabled) to enable the firewall on the modem and they have manufactured thousands of these devices. BSNL FTH provides public IP to all the users (but that IP is not static and keeps changing). Since the IP is public the modem is reachable from anywhere on the Internet. The username and password for this modem is: root, admin. BSNL officials don’t change this password during installation. And as per my analysis on a small sample on their network, 91% of the devices have default username and password. That’s obvious because most of the consumers don’t have the technical know how to enable firewall or reset password themselves. Now the implications of this is that all the users have their default username and password enabled on there public facing modem.
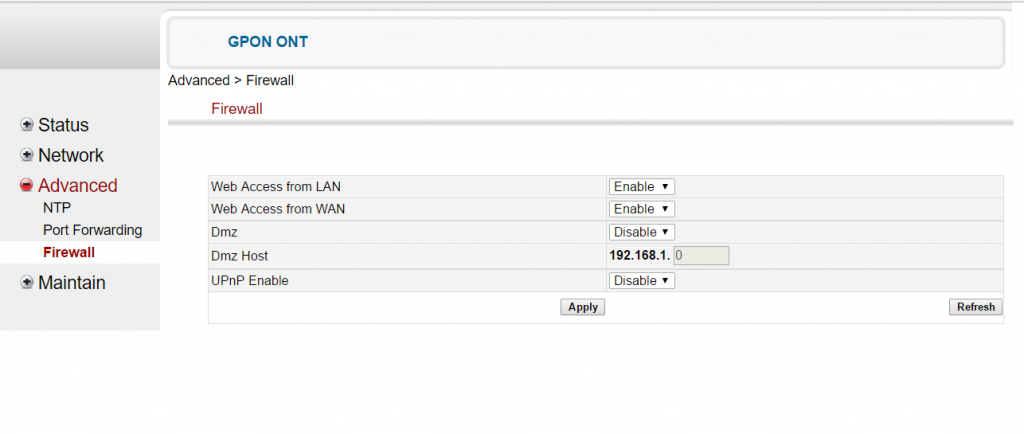
In the picture above, you can see the firewall options. If Web access from WAN was disabled by default then this attack would not have been possible even if default username and password was set. But for some reason they didn’t turn it on by default and that’s the reason why 91% devices can be remotely modified. Now the problem is that
- Even if you enable it from admin console and you reset your device then you have to re-enable it again.
- If you have changed your default username and password then also you are not safe. Why? Because the modem uses basic http auth which can be brute forced[ref]http://security-geek.in/2014/08/22/using-burp-suite-to-brute-force-http-auth-attacks/[/ref]. You must disable Web Access from WAN for your safety.
And here’s a one line script which can disable the internet on a device if it has default username and password.
curl <some payload> http://<public-ip>/html/wan.html
** For obvious reasons I can’t disclose the payload but it’s no rocket science to figure it out. If you know basic html, then you can figure it out after accessing the admin console of the modem. Let’s leave it at that.
Other possible attacks:
You can do port forwarding and get inside their home network to see what they are doing. This might be a little tricky but not entirely impossible to do
The script:
# Please note that I can’t give away the scripts or mention the complications of the attack because of obvious reasons. But I will give a pseudo code for it.
Attacking the whole BSNL FTH Network.
- Scanning the network
- Using the data available on tracemyip you can get the IP subnets which BSNL uses to provision Internet to their users. Yes you might miss out on many users but using some advanced scanning techniques (which are out of the scope of this blog) you can cover a lot of users.
- Launch the attack on all online users.
- Carefully craft a script which logs in to their routers and uploads a payload which disables their internet. Payload is nothing but a post request which has some data.
- Multi-thread the attack to attack thousands of users at a time.
- Spawn threads for each IP subnet which you have found and launch a massive attack. Within a few minutes more than 90% of BSNL users will get offline.
This attack can be launched from anywhere in the world and can be made untraceable using TOR. It can bring down BSNL’s internet for weeks.
What can BSNL do to solve the problem?
- A remote patch which can solve this issue for all the users (A remote patch is indeed possible and I have written one too).
- But this won’t work if the users reset their modem.
- Firmware itself has to be patched for the new devices.
- For older devices advisory has to be published on the website with instructions on how to reset default router password and disable web access from wan on router.
What to do if you are a BSNL FTH User?
- Immediately disable wan access to your admin console.
- Repeat this process whenever you reset your modem.
- Change the default username and password of wifi devices connected to your FTH device.
- Even if you are not a BSNL FTH User, then also make sure that login from wan is disabled on your router and also change default username and password.
Please note that I haven’t discovered something new or “hacked” anything. I am just bringing into notice the negligence of BSNL towards its customers. Yes you can argue that the default username and password problem has been there for ages but most of the modems don’t allow logging into the router from WAN and that’s why they are safe (Yes there may be many other modems with other vendors as well who might have the same issue but I’m not aware of them).
Please share this so that it reaches a mass number of people because then only we can force BSNL to act. Thanks.
UPDATE, 5th November 2016:
BSNL did reply to me on twitter on November 1st but they are yet to do anything about it. The bug remains unfixed.
UPDATE, 19th December 2016:
Still no response from BSNL. I guess they don’t care. Bug remains out in the open.